On 27-Dec-2025 19:25:11:
I deployed Anubis so that I could make the cgit server public again. The default config seems to work well but I enabled the whitelist for known git clients just in case. If git cloning breaks just use the GitHub mirrors.

On 27-Dec-2025 16:03:03:
Since the official page is so slow, I made a page to track whether or not there is a sportsball game.
Is There A Sportsball Game Today?
On 18-Feb-2025 23:12:26:
This is the table header
This is more data for the table header
This is the first row of data
This is more data for the first row
This is the second row of data
This is more data for the second row
This is the table footer
This is more data for the table footer
The joke is that there is a cake on the page, but I put it inside of the second caption so that it is invisible to Firefox. If you are using Firefox and would like to see the cake, you will have to open up Chrome.
This bug is so old it may have actually been invalid when it was filed. The HTML standard does not allow multiple <caption> tags on a table. Although just because its not allowed doesn't mean that people don't do it. On top of that, the CSS standard allows you to assign table like behavior to arbitrary HTML elements without putting any prohibition on having multiple captions. The "table" above is actually made from <div> tags that are assigned table like behavior via CSS. I added some extra rows/cells to the table just so you can see it in action.
Despite the claim in comment #39, this does occur in the wild. Comment #37 mentions it occuring on an Atlassian Confluence site, although its unclear if it is Confluence itself or a Confluence plugin that is generating multiple captions. There is also a linked bug (1926229) that documents it on a weather site. Although the weather site appears to have changed their layout to work around the Firefox bug.
On 24-Feb-2023 20:00:03:
I got so frustrated by DTE's outage center that I wrote my own.
On 18-Feb-2023 13:41:07:
I'm sure this isn't exactly news to Windows sysadmins, but as a Linux user I was just shocked to find out that Microsoft hasn't changed the Windows password hashing algorithm since the very first release of Windows NT in 1993. What is that algorithm? Unsalted MD4!
I wanted to see just how bad that actually was in a similar format to the nice infographics that Hive Systems made for MD5. So I made difficulty table generator. Here is the table for MD4 on an RTX 4090:
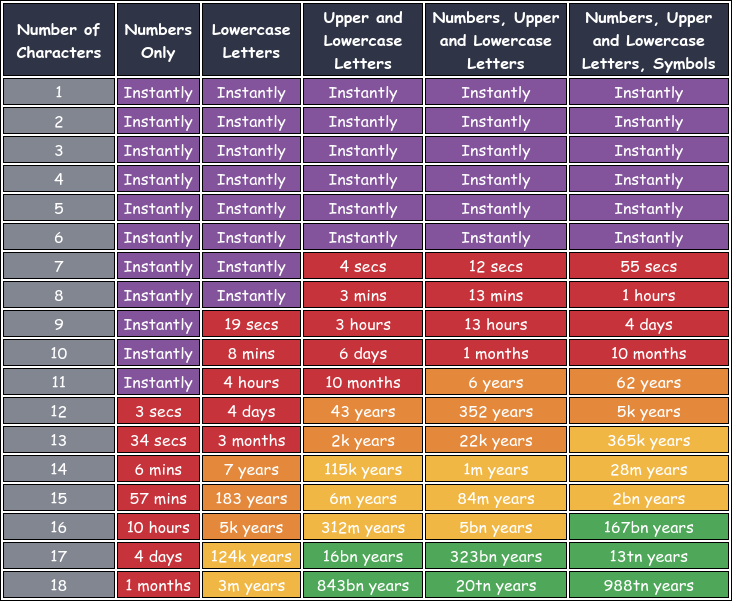
Some notable things:
- At least on a GPU cracker, the 1979 UNIX DES hash (first released with System 7) is stronger than the 1993 Windows MD4 hash for any given password complexity.
- Although weak by modern standards, the 1995 UNIX MD5 hash (designed by Poul-Henning Kamp for FreeBSD) is notably stronger than plain MD5. (The original UNIX DES hash appears to also be stronger than plain MD5!)
- Raw hash power (what is shown in these tables) is not the full story on algorithm strength. DES's Achilles Heel was the 8 character maximum length. Salting passwords also increases the strength in ways not shown in these tables.
- Windows Lan Manager hashes were two independent 7 character DES hashes and case insensitive, which results in a pretty unique table.
- All hail bcrypt!
On 29-Sep-2021 14:22:22:
This is a followup to my previous post about issues with the ACPI implementation in my Dell Latitude 7410. I had been hoping that some firmware update would fix it but nothing has. Then I saw an article on Hacker News titled Do not leave XPS laptop in any sleep/hibernate/standby mode when placed in a bag which linked to an article on Dell's website titled FAQ Modern Standby.
The main point from Dell's FAQ is this quote:
Under no circumstances should you leave a laptop powered on and in any sleep/hibernate/standby mode when placed in a bag, backpack, or in an overhead bin. The laptop will overheat as a result of that action.
Wait, what? The entire point of sleep and/or hibernate is being able to put the laptop in a bag while moving from one location to another! While this "Modern" Standby may be fine (and even desirable) for people who put their laptop on a desk and then never move it, its very much not okay for people who actually use their laptops as portable computers.
Modern Standby is, in technical terms, called Low Power S0 Idle. This is quite a bit different from the traditional S1 Standby, S3 Sleep (suspend-to-ram), or S4 Hibernate (suspend-to-disk). In fact traditionally S0 meant the system was fully powered on. This new Low Power S0 Idle may consume less power than the fully powered on S0 state, but it consumes a lot more power than the traditional S3 sleep. More power == more heat. This is why Dell is now saying you can't store a sleeping laptop in a backpack.
You can probably guess how this relates to my laptop's sleep issues at this point...
Support for Lower Power S0 Idle is incdicated by a bit in the Fixed ACPI Descriptor Table or FADT. And if I dump the table on my laptop I see this:
Low Power S0 Idle (V5) : 1
So the laptop's firmware is advertising support for this new Modern Standby. Taking a look at the contents of /sys/power/mem_sleep indicates that Linux has detected this and is using it for the preferred sleep mode:
[s2idle] deep
And this is also reflected in the dmesg output when the kernel goes into sleep mode:
PM: suspend entry (s2idle)
Ugh...
Luckily this is Linux, not Windows, and we can easily override crap like this. After running echo deep > /sys/power/mem_sleep it now shows:
s2idle [deep]
And this is also reflected in the dmesg output:
PM: suspend entry (deep)
And like magic the laptop no longer comes out of sleep mode when the lid is closed! The amount of power consumed and heat generated is also greatly reduced.
Bad news: The fix above only works as long as the laptop still supports S3 sleep. My coworker has a Dell Latitude 7420 (one model newer than mine) and reports that it no longer advertises S3 sleep capability. Dumping the ACPI DSDT off of his laptop suggests that it does support S3 sleep but its disabled. He is going to poke through the firmware settings to see if it can be re-enabled.
So in summary:
For two decades its been safe to put a sleeping laptop in a backpack. Now vendors have decided to change the default behavior of sleep mode in a way that makes this unsafe. This can easily cause the laptop to overheat, reducing the lifespan of the laptop. This is a clear violation of the principle of least surprise.
On 24-Mar-2021 01:36:40:
So last year I got a new Dell Latitude 7410 laptop at work. Recently some other coworkers were getting new laptops and they asked about this one. One specific question that I was asked was whether or not suspend to RAM worked properly. I told them it was working fine.
I was wrong, I was so wrong. Today I discovered that it only appears to work fine. The truth is that it is actually very broken in a non-obvious way.
The default behavior of suspend to RAM on most operating systems is that it automatically enters suspend on lid close and automatically resumes on lid open. If that is how you want suspend to work, then it works just fine on the laptop. Of course if you frequently close the lid on your laptop to walk to another room at work you might chose to disable this and have the laptop enter suspend only if the user explicitly tells it to. You might also set it to not wake up until the power button is explicitly pressed. These are normal user configurable settings. I'm too lazy to reinstall Windows on this laptop but I'm guessing those settings don't work right on Windows either. I'm not even sure its possible to work around this particular ACPI bug from the OS.
Lid close is an unconditional ACPI wakeup event!
Whiskey Tango Foxtrot?!? If you put the laptop in suspend to RAM and then close the lid, the laptop wakes up. I cannot fathom any situation in which this is desirable behavior.
Okay, but you can usually disable individual wakeup events from the OS. On Linux you do it in a file called /proc/acpi/wakeups. If you cat the file you'll see a list of all the possible ACPI wakeup event triggers and whether or not each trigger is enabled. If you echo the name of one of the triggers into the file it will toggle the enable/disable state. The list is kind of big, so here are the ones that show up as enabled when Linux boots on this laptop:
RP05 S4 *enabled pci:0000:00:1c.0
PXSX S4 *enabled pci:0000:01:00.0
RP09 S4 *enabled pci:0000:00:1d.0
RP13 S4 *enabled pci:0000:00:1d.4
XHC S0 *enabled pci:0000:00:14.0
LID0 S3 *enabled platform:PNP0C0D:00
PBTN S3 *enabled platform:PNP0C0C:00
LID0 is the lid switch. This is the event you disable if you don't want your laptop automatically waking up when you open the lid. On every previous laptop I've ever used this LID0 is only a wakeup event on lid open and never on lid close. After all, why would you ever want the laptop to wake up if you're closing the lid? Okay fine if this laptop wants to be weird we can echo LID0 into the file to disable it. Thats not a big deal, I don't want a wakeup event on lid open anyway.
Except this toggle doesn't actually work! Even with it set to disabled both lid open and lid close remain ACPI wakeup events. My immediate thought was to blame Linux, but I don't think this is a bug in Linux. I went into the BIOS (which is not actually the right name for it anymore, but everyone still calls it that) which has its own options for controlling lid switch behavior. These BIOS settings also do not work which suggests that the problem lies in the firmware and is not something the OS can control.
Another indication that this is not a bug in Linux is that other events do toggle properly. I discovered that unplugging the USB-C power adapter is also an ACPI wakeup event. I traced this behavior to the RP05 event and was able to disable it from Linux. So toggling wakeup events from Linux actually does work, just not for the lid. The ACPI firmware itself must be buggy and ignores any attempt to disable wakeups on lid events.
On top of all of this Dell decided the laptop didn't need a power LED so if the lid is closed there is no clear indication of whether its still in suspend or if it woke up. I had to debug all of this using a USB mouse flipped upside down as a crude power indicator. I also tried upgrading the BIOS from 1.1.1 to 1.5.2 but that didn't help.
I'm not an ACPI expert but I have every reason to believe this is a bug in the ACPI firmware and there is nothing the OS can do about it. If this works correctly on Windows then it is only because Microsoft has some impressive workaround. Most OSes have workarounds for ACPI bugs, but I'm not aware of any way to disable an ACPI wakeup event if the firmware is ignoring the normal interface that the OS would use to do that. The only OS level workaround for bogus wakeup events that I can think of is to just immediately go back into sleep if the OS thinks that the wakeup event was bogus.
So I have no choice but to use the default Windows behavior of having lid close trigger suspend to RAM and lid open trigger resume. This is the only way to avoid the rogue ACPI wakeup event that occurs when the lid is closed. I'm okay with the latter, but I really do not want the former. Or do I... Linux is still in full control of exactly what happens when a lid close event occurs. If I want lid close to mean suspend to RAM but only during a full moon and at any other time it should say "I'm sorry Dave, I'm afraid I can't do that" over the speakers, then I can make it work that way. Or more usefully, I can make it check to see if the screen is locked.
So with my workaround in place the actual act of suspending is triggered by the lid close event, but it only happens if the screen is already locked. This allows me to carry my laptop around with the lid closed without it going to sleep and still have working suspend to RAM.
On 10-Jun-2018 13:54:19:
I just realized i never posted about it here, but a while back I wanted a simple ACME client for handling my Let's Encrypt SSL certificates. I found a nice and simple one for doing http-01 challenges that was named acme-tiny. I made a fork of the original client which does dns-01 challenges instead. This also means it can handle wildcard certificates! (The original can't do wildcard certs because http-01 auth doesn't support them.) You can get my fork from:
There is a distinct pattern where I mostly work on it every 90ish days when I renew my LE certificates.
Disclaimer: I've never really tested the dynamic DNS support, someone sent me that as a pull request.
On 10-Jun-2018 13:38:01:
MFW I write a program that might actually be useful enough to put a proper license on.
OpenSSL does not support converting an elliptic curve private key from using explicit parameters to using a named curve. So I wrote a program to do that.
Github repo
Local mirror (cgit > *)
Archived Entries


